When articles began to surface about suspected Chinese infiltration attempts into thirty of the biggest tech companies in the world which include Apple and Amazon, I wasn’t sure whether it was the opening promo for the next James Bond movie or the real deal.
If in fact if these allegations prove to be correct it means that the current mega shift in geo politics and trade wars that has begun between the United States, Australia, Germany and China have a far more sinister and calculated objective. and will rapidly expand to include more and more countries and companies.
Many politicians and mega media-outlets have attempted to portray these events as no more then the rantings of a mad president who is having a temper tantrum. In truth, the reality that we find ourselves in couldn’t be further from that.
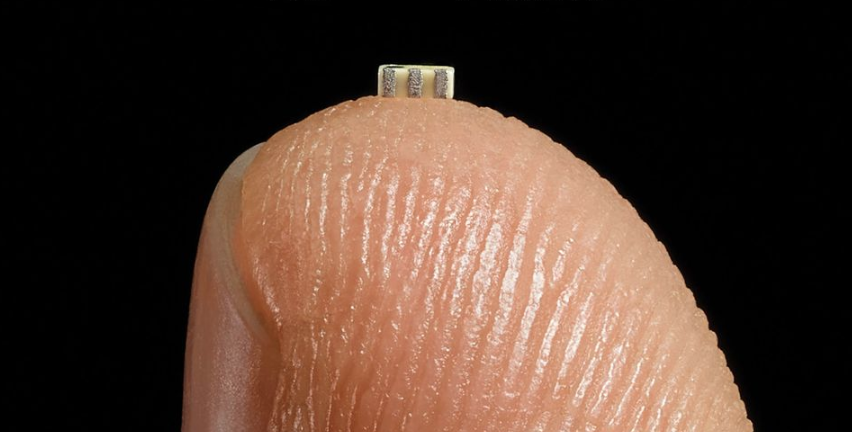
It has been reported that “mini micro chips” were first discovered by Amazon in 2015 while performing due diligence after they acquired a video service provider firm called Elemental for $500 million.
AWS then performed an additional due diligence while investigating the possibility of purchasing technology from “Super Micro Computer Inc” via a third party company and discovered that there were secret hidden chips imbedded deep inside the mother boards of the video streaming tech. The investigation has been ongoing ever since.
This obviously means that the US government and its leaders are also fully aware of this information as well as a lot more information that has either not yet been discovered or has not been exposed. If these allegations prove to be correct it means that the Chinese government have implemented a long term project of illicit intelligence gathering and information theft at scale never before imagined even in the best science fiction novels ever written.
This means that not only have the Chinese been able to collect all of the personal data from all of the devices that contain the “Supermicro mini chips” but also all of the geo tag information regarding people movement and of course all of the transactions, text, image and video communication performed using the compromised servers, hardware and mobile devices.

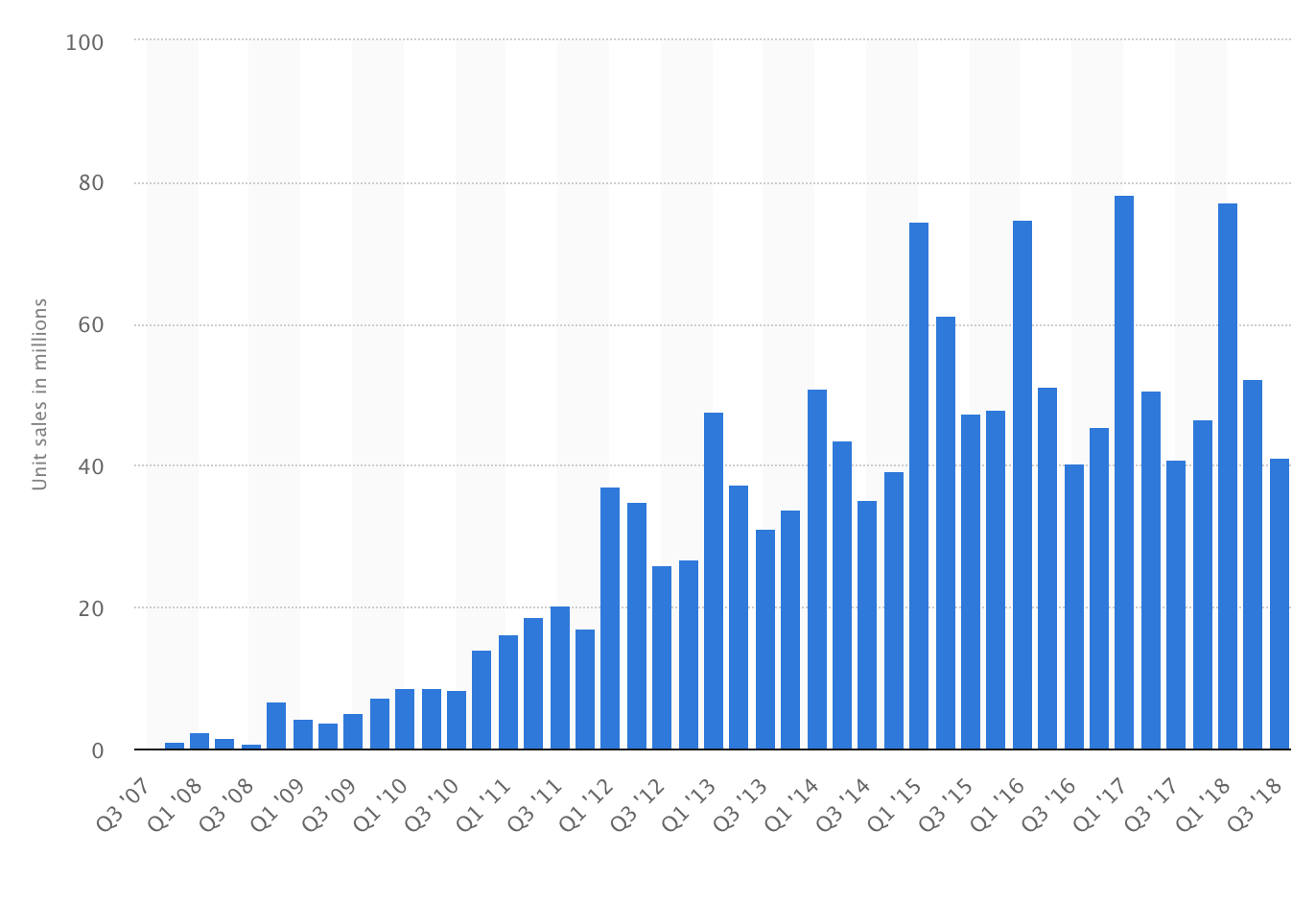
Apple iPhone Sales – 2007 – 2017
Apple alone has sold more than one billion iPhones (Made in China) worldwide from 2007 to 2017. If you consider the fact that old iPhones are not destroyed but rather repurposed and resold to emerging markets, it means that the data collection mechanism is growing and spreading across the globe.
Investigators found that the microchip problem affected almost 30 companies, including a major bank and government contractors. Bloomberg
As the potential ramifications of the massive cyberattack continue to play out, the Trump administration has made computer and networking hardware, including motherboards, their focus for the latest round of trade sanctions against China. White House officials have also made it clear they think companies will begin shifting their supply chains to other countries as a result.
If true, this means that the Chinese government may have been harvesting data from two of the world’s largest corporations and service providers since 2014 – all with a microchip the size of a grain of rice.
Chinese Economic Policy and Governance
As China is a communist country with a completely regulated economy there can be no doubt that this is not the act of an individual lone wolf player in the business world but rather the pre-meditated act of a government with years of planning, execution and of course the eventual discovery of this sinister act of war. I say this because anyone who gives it just a moment of though will realise that something like this would eventually be discovered.

This means that the objective is not the act of information gathering and collection per say, but the collecting of specific information, plans, details on specific topics for specific and focused means and objectives that are yet to be fully understood.
China is well placed to carry out this kind of attack, as 90% of the world’s PCs are made in the country. Carrying out an attack of this magnitude would involve developing a deep understanding of a target product’s design, manipulating components at the factory, and ensuring that the doctored devices made it through the global logistics chain to the desired target locations.
Having a well-done, nation-state-level hardware implant surface would be like witnessing a unicorn jumping over a rainbow. The Guardian
Apple had deployed about 7,000 Super Micro servers when the company’s security team found the tiny hidden added chips. Apple discovered the compromised servers in 2015 and reported the issue to the FBI,but kept details about what it had detected tightly held, even internally.
These chips would allow potential hackers to createa stealth doorway into any network that included the altered machines.This level of hardware hacking would be unprecedented in scope, and theBloomberg report claims that the FBI opened an investigation after the incident was reported by Apple that’s still in progress three years later.
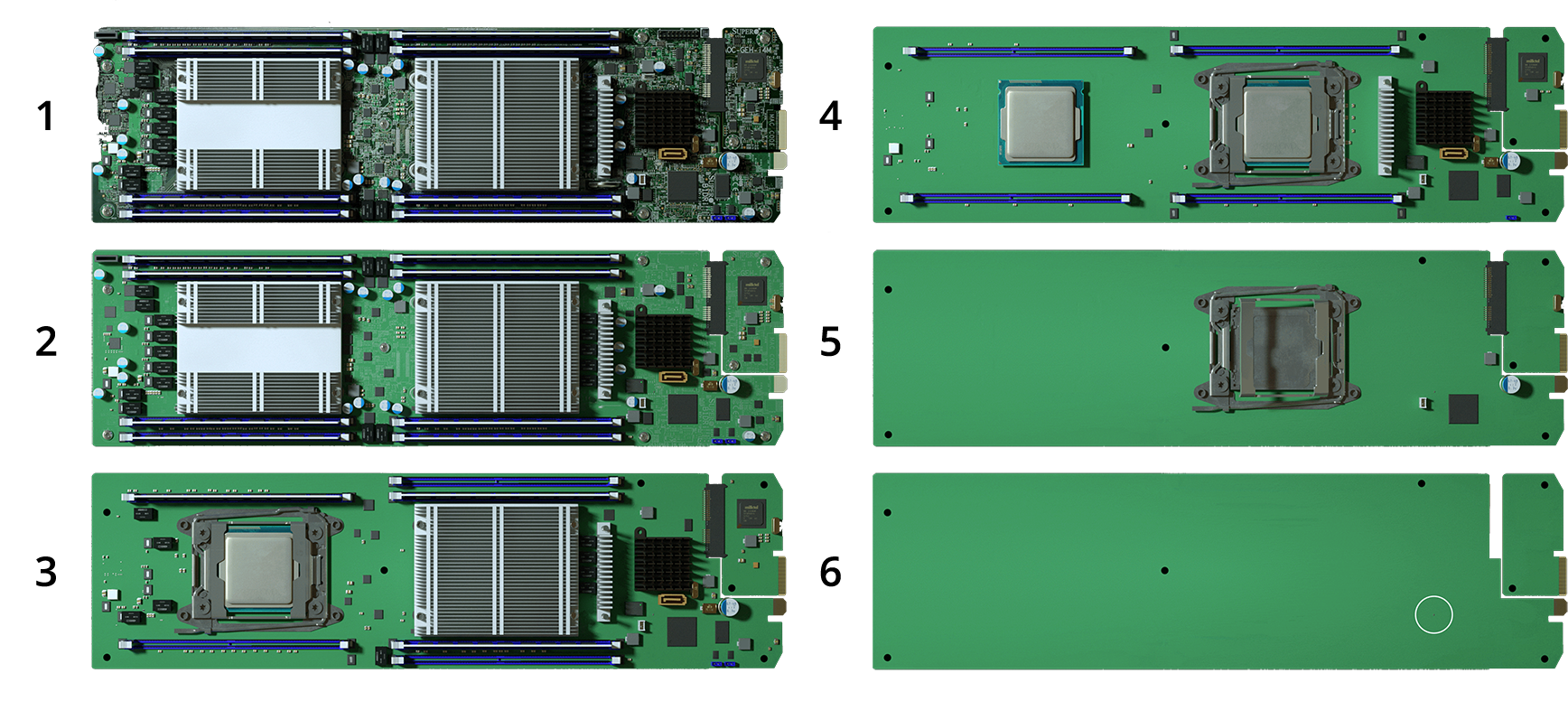
Chinese Motherboard Breakdown
The mini micro chips about the size of a grain of rice were inserted into the production line of the mother board. The motherboard breakdown image shows the exact size, shape and position of the sinister Chinese tracking chip circled in image number six within the white circle in image 6.
Protecting the Client Base
Of course all of the affected companies deny any prior knowledge of the chips presence such as AWS or flatly deny that any of their products have been compromised at all such as Apple inc. Three Apple employees refute their companies claim and stated that Apple was also a victim of these attacks.
The companies’ denials are countered by six current and former senior national security officials, who in conversations that began during the Obama administration and continued under the Trump administration detailed the discovery of the chips and the government’s investigation.
G_d Mode – Level Attack
The level of infiltration that this type of hardware technology insertion could pose, has a massive impact on many companies and supply chain service providers. An attacker could use this kind of malicious implant to bypass all software protection mechanisms, a doomsday scenario for software and hardware security defenders.
China has often been suspected, but rarely directly implicated in Orwellian spy campaigns based on hardware manufactured in China. As the majority of electronic components used in U.S. technologies are manufactured in China, this is a point of concern.
Companies including component manufacturers such as Huawei and ZTE, as well as the surveillance camera manufacturer Hikvision, have all fallen under intense suspicion from the U.S. government in the past year. The Australian government has already effectively blocked Chinese carriers from building the country’s first 5G network in August of this year.
Market Reaction to the Chinese Espionage Claim
In reaction to the exposure of these incredible apocalyptic allegations the stock market began to react as of late Thursday afternoon. The shares of computer maker Lenovo fell about 20 percent on Friday morning as shares in many Chinese tech firms struggled for gains during Asian trading hours.
Shares of the iPhone-maker fell 1.75 percent and Amazon declined about 2.21 percent in Thursday trading. Shares of Super Micro plummeted more than 40 percent following the report.
Supermicro
Supermicro’s extensive list of clients in 2015 is what made them a juicy target, a former intelligence official told Bloomberg. In addition to Apple and Amazon, their servers can be found in the Department of Defence data centres, the CIA’s drone operations, the onboard networks of Navy warships, the Department of Homeland Security, NASA, and the House of Congress.

Global Security Compromise
If these allegations prove to be correct it means that all of the discussion about the new cold/trade war currently flying around the world media and being screamed about by politicians being implemented by the Trump administration are based upon a completely different set of variables. The security of the global technology supply chain had been compromised, even if consumers and most companies don’t yet realise it.
“ Think of Supermicro as the Microsoft of the hardware world,” a former US intelligence official told Bloomberg. “Attacking Supermicro motherboards is like attacking Windows. It’s like attacking the whole world.”
Conclusion
The allegations of Chinese infiltration attempts if they prove to be true, are so big a deal that I don’t think anyone can fully comprehend the ramifications that this exposure may produce. At the very least, it will cause international manufacturers to completely relocate their productions facilities and supply chains to friendly of safe geographical locations, and in a more pessimistic scenario something of this magnitude could even lead to international conflict eventuating in all out war.
No matter who one looks at the events as they unfold, it is becoming more and more apparent that the Chinese appetite to influence world affairs is definitely growing as is their ambitions economically and militarily on the world stage.
Related Articles
If you wish to expand you knowledge about China and the Chinese click on the links to end the following articles.
Pixel Accurate UX Designs
When designing a new product UI, I alway try to employ the K.I.S.S method, of "keep it simple stupid", it hasn't failed me yet. If on the other hand you have no choice but to create a new custom control then provide the developer with a "pixel accurate" screenshot...
How to Prioritize your Product Backlog
A product backlog is the definitive list of all the new epics, features (changes to existing features), user stories, bug fixes, infrastructure changes and maintenance items of your software product. It is also the place to add any other additional tasks that a...
UX Prototyping – The Only Way to Fly
Creating a software solution is a labor intensive human endeavour. It requires input from many different disciplines and stakeholders for it to reach fruition. So, before you start to crunch code maybe you should give some thought to first building a full interactive...

Recent Comments